Exploring OpenCASE: Priority 2 - Protect your people
Table of Contents
In the previous article, we covered why protecting your user accounts should be the absolute top priority for small enterprise cybersecurity. In this article we’re going to take a closer look at the next most important thing…
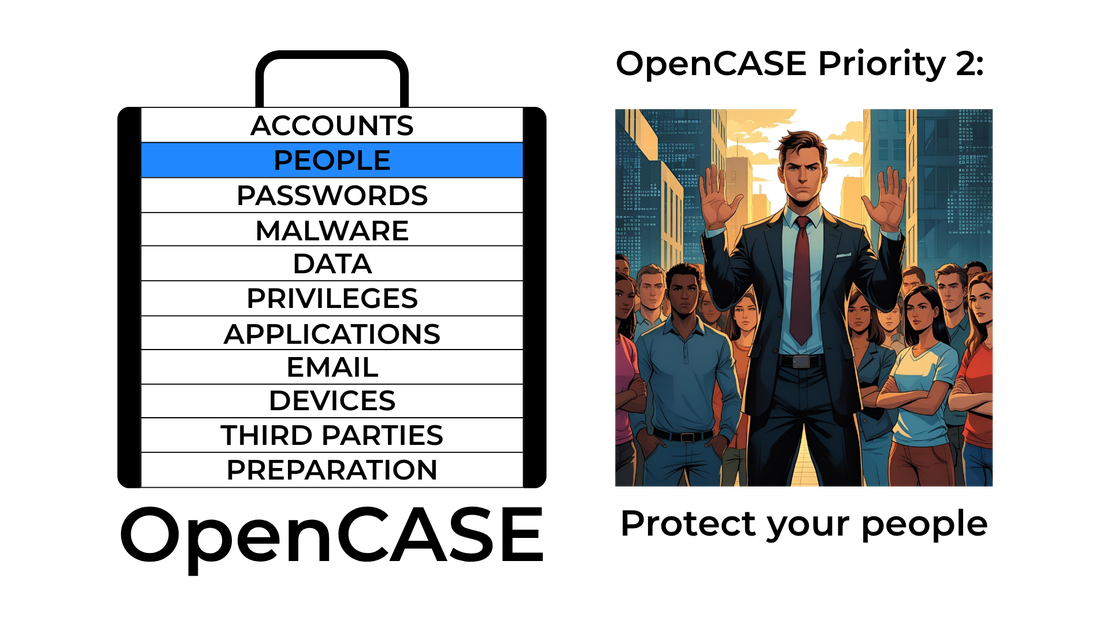
Priority 2 - Protect your people.
You’ve all heard the witty cliches: people are the weakest link in cybersecurity; humans are easier to hack than computers; Your users are your biggest vulnerability. Ha ha, yes, very clever.
Victim blaming aside however, these cheap taglines from the cybersecurity awareness bargain bin belie a harsh truth: most businesses still think of cybersecurity primarily as a technology problem, and therefore assume it can be solved with technological solutions. They invest all their available time and resources into fancy tools and dashboards. Meanwhile they spend nothing on education and training for their staff, don’t allocate any time for professional learning, and do nothing to promote a culture which values cybersecurity and good cyber-hygiene habits.
Is it any wonder then that your people are the weakest link?
These observations apply doubly in a small business context, because without knowing any better themselves, “cybersecurity” often boils down to whatever their MSP (re)sells to them. If they are lucky, there might be a simulated phishing tool in there or some pre-canned security awareness videos. More often than not however, it’s just some combination of tools designed to mitigate technology risks: anti-virus, application control, browser content filtering, etc.
The great irony of this approach is that small businesses generally have the least amount of money to spend on cybersecurity tools. If given the choice by their MSP they will usually opt for a cheaper managed services plan without “advanced cybersecurity” rather than fork out an extra $20/user/month.
On the flip side, a lot of the most effective people-based mitigations cost “nothing” (i.e. there’s no up front cash outlay required). They are process controls, or cultural controls. Even when they’re educational, that doesn’t always have to mean spending money on training courses - often it can just be having the right conversations with your staff, or giving them time to follow their own curiosity.
So it is that one of my biggest and longest standing pet peeves when it comes to many cybersecurity frameworks - particularly ones which are pushed at small business - is that they have little to nothing to say about protecting your people, and when they do, it’s always presented as a lower priority: something to be tackled once all the technological stuff is in place. This backward approach tells me a couple of things: the framework isn’t really designed with small business in mind, and/or the people who wrote it have no real experience trying to build cybersecurity capability in small business.
When I designed OpenCASE, making sure that small enterprises understand the importance - and superior ROI - of investing in the human elements of cybersecurity was one of my top priorities. So here it is: Priority 2 - Protect your People!
Implementation Level 1 - Embed cybersecurity into staff on-boarding and off-boarding processes.
The first step to building a strong cybersecurity culture in your small business is making sure you clearly communicate your expectations to them, and that they understand their responsibilities, from day 1 on the job. It pays to be prepared in advance: have everything documented so can spend some time going through it with them, and they have something to take away and refer back to later. This approach gives you peace of mind that they didn’t just skim through everything without really paying attention. Ask them to sign the document as a formal acknowledgement so they will appreciate that they’re now are accountable for their actions.
You’ve probably already got a checklist of tasks for when a new person starts work - making sure they have a computer, their user accounts are set up, and they have access to all the right things is pretty standard these days. Don’t stop there however, help them get their multi-factor authentication set up, how to use their password manager, where to save their important files - and anything else you can think of! Make sure they have the knowledge and tools to live up to the expectation you just set for them.
Try to take a similarly structured approach when a staff member leaves. Properly off-boarding users is just as important as on-boarding them. Make sure they return all your company property and data. Remind them of their obligations for confidentiality. Lock their accounts and revoke their access to all your online systems and applications.
Implementation Level 2 - Appoint a cybersecurity champion.
Cybersecurity culture doesn’t just happen. It has to be built - and nurtured. A cybersecurity champion is the person in your organisation who is responsible for making that happen.
Crucially, being a cybersecurity champion doesn’t mean having to be a cybersecurity expert, or being responsible for training the rest of the team. It’s more about making sure that cybersecurity is something that your staff are comfortable talking about and interested in engaging with - keeping it on the agenda and on people’s minds.
Being a cybersecurity champion doesn’t need to be a lot of work either. Something as simple as finding and sharing interesting cybersecurity news with the rest of the team can make a huge difference just by helping to promote awareness and get people talking about the topic.
Being cybersecurity champion can also be a great professional development opportunity, a way for people in different roles to dip their toes into the world cybersecurity. The best champions will be people who have some sort of interest in cybersecurity to begin with, they will bring natural curiosity and passion to the role which will make them all the more effective.
Implementation Level 3 - Incorporate cybersecurity into professional development.
When it comes to cybersecurity awareness education, most people just buy an off-the-shelf product and call it a day. The content in these tools tends to be very cookie-cutter in nature, and not very engaging to the average worker (though it has gotten a lot better in recent years). There’s certainly a place for these tools, but relying on them as the central pillar of cybersecurity education in your organisation will not lead to great outcomes - we all know most of us are just clicking next-next-next or watching on fast forward then guessing the very obvious answers to the quiz at the end….
Especially in a small enterprise context, cybersecurity education needs to be more than a box ticking exercise. Just being able to answer a few quiz questions or correctly identify the fake phishing emails they get sent is ultimately not going to make a huge difference to a small business’ risk profile, because the staff still don’t really care - they’re not invested in the outcome. Getting your staff to be interested in cybersecurity at all is the first challenge, then you have to keep them engaged, and finally to understand that whatever their jobs is, cybersecurity is an integral part of it.
The OpenCASE approach to cybersecurity education aims to get people more engaged and invested in their own cybersecurity education by giving them agency in selecting - and accountability for meeting - their own learning outcomes. It recognises that every person will have differing levels of cyber-literacy, differing interests, and their own preferred ways of learning. Whether or not everyone can reach the same standard of competency or understanding is not the point - it’s whether your staff care as much about protecting your business as you do…
(they don’t, but they might at least pretend to if you don’t make it a chore for them).
Conclusion
I’ve long believed that too much of the cybersecurity advice available for small business is focused on tools and technology. OpenCASE aims to address this by making sure Protecting Your People gets the attention it deserves at Priority 2. It’s undeniable that technology controls are essential to cybersecurity, but in a small business context the cost-benefit of investing in your people cannot be over stated.
Stay tuned for the next thrilling episode of “Exploring OpenCASE” soon!